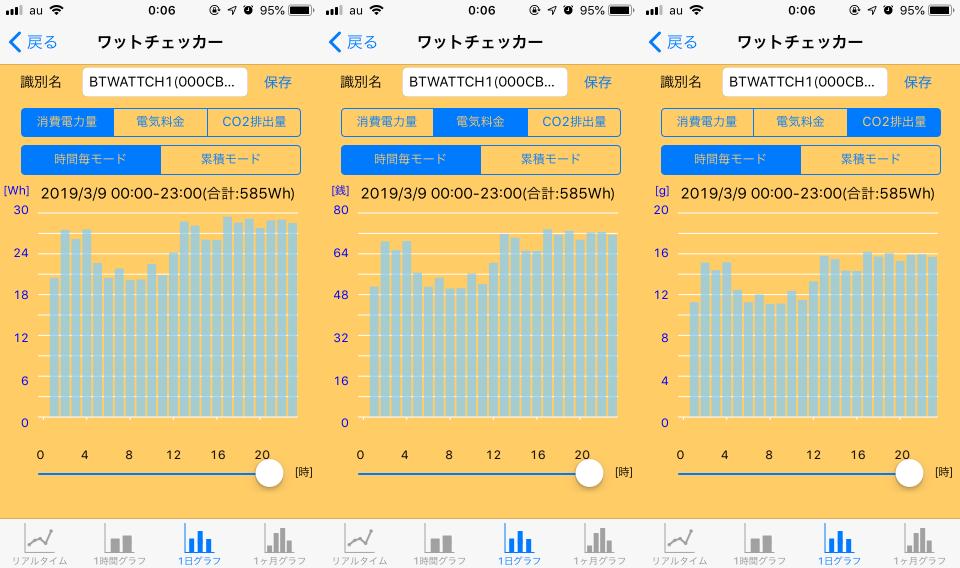
Yokogawa Electric introduces ServiceNow as a security operation base: Enterprisezine
ServiceNow Japan has announced the introduction of ServiceNow's "SECURITY Operations" as an operation base for Yokogawa Security Operation Center (Y-SOC), a security monitoring center developed by Yokogawa Electric in the company.
Yokogawa Electric developed Y-SOC based in Bangalor in April 2018 to enhance the security of the entire group.To date, Y-SOC, which has been monitoring security in 15 locations worldwide, collects IT systems events and security logs, develops suspicious communication, detection, analysis, and automatic detection programs, automatically.It is said that alert notifications are being implemented.
In order to further enhance security, ServiceNow's "Security Operations" and "IT Operations Management" are used as the Y-SOC operation base.Introduction, the introduction of IT Operations Management in January 2020, visualized about 30,000 devices, including servers and routers introduced in the group, and at the same time, when new vulnerability information was released.However, it is also possible to timely extracted whether it affects the system introduced by Yokogawa Electric.
Furthermore, by linking with various Y-SOC tools, it is possible to refer to CMDB (configuration management database) and prioritize when security incidents are automatically incurred, reducing security incidents and reducing security incidents.It has been reported that the response work has been 30%efficient.
In addition, the introduction of Security Operations was launched in April 2021, establishing two workflows for security incidents and vulnerability.It is now possible to seamlessly run from security analysis to containment, eradication, recovery, and reviews.Specifically, when alert notifications from Y-SOC etc. are pushed in real time, Security Operations will refer to multiple cyber threat intelligence information.For those with high threats, the company has created an automatic defense mechanism with IP addresses, URLs, domain names, etc., and automates blocking communication to security products.This has previously been a threat and it took 1-3 weeks to block, but it can be reduced to about 1 minute after the workflow was created.
In addition, in the vulnerability workflow, information on vulnerability scanners is imported into Security Operations, and priority is based on whether the target system has vulnerabilities while referring to CMDB, and the risk assessment.You can also assign the corresponding correspondence to CSIRT (Computer Security Incident Response Team).In addition, by linking with the existing IT Service Management, the IT department and Y-SOC have also achieved smooth cooperation.
[Related article] ・ Utilizing NTT Data Technology and ServiceNow to solve IT service management issues.Makridi becomes inauguration




![[EV's simple question ③] What is good for KWH, which represents the performance of the battery?What is the difference from AH?-WEB motor magazine](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/9/b2506c4670f9f2cb45ffa076613c6b7d_0.jpeg)
![[How cool is the 10,000 yen range?] 1st: The performance of the "robot vacuum cleaner with water wiping function (19800 yen)" like Rumba is ...](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/25/5251bb14105c2bfd254c68a1386b7047_0.jpeg)